2025/06/20 [重要] フィッシングメールに注意
本日下記のようなフィッシングメールが本学あてに送信されて来ています。
件名:
ドキュメント「支払確認領収書.pdf」がOneDrive経由で共有されました
メール本文のリンクはクリックしないようにしてください。
うっかりフィッシングサイトにパスワードを入力してしまった場合は、すぐにパスワードを変更し、最寄りの情報イノベーション課までご連絡ください。

本日下記のようなフィッシングメールが本学あてに送信されて来ています。
件名:
ドキュメント「支払確認領収書.pdf」がOneDrive経由で共有されました
メール本文のリンクはクリックしないようにしてください。
うっかりフィッシングサイトにパスワードを入力してしまった場合は、すぐにパスワードを変更し、最寄りの情報イノベーション課までご連絡ください。
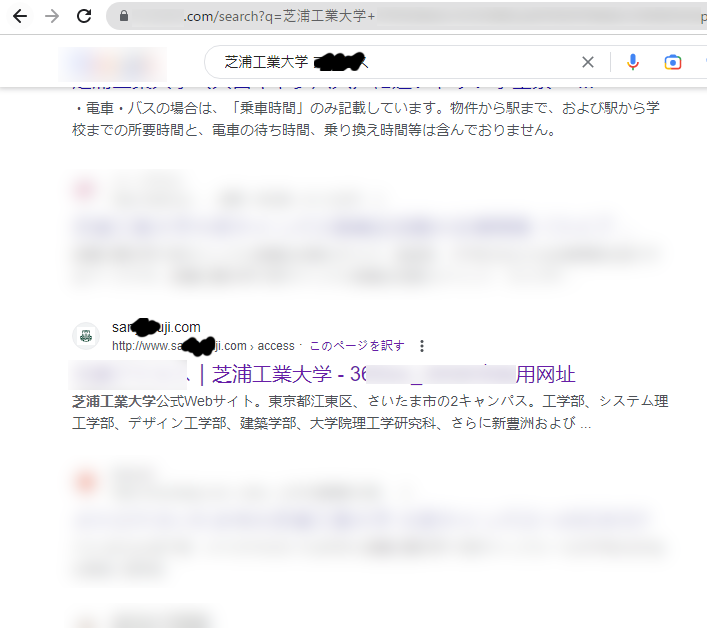
検索サイトから本学に関連するキーワードを検索すると、本学を騙る偽サイトが検索結果に表示されることを確認いたしました。
本件に限らず、最近検索結果に偽サイトが表示されることが散見されます。
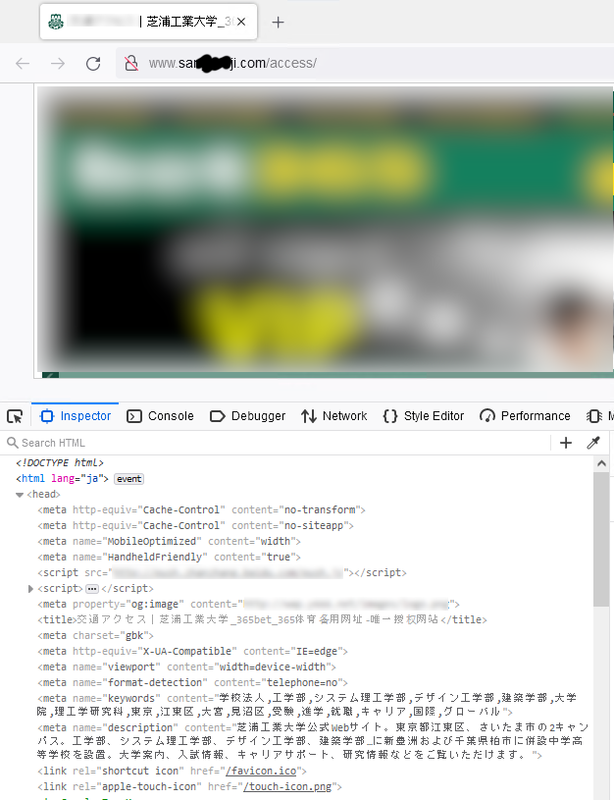
偽サイトの中にはアクセスをするとWebブラウザに感染するものや、マルウエアがダウンロードされるものも存在しますので、常に検索結果に不審なものが含まれていないか確認することを心掛けてください。
また、偽サイトを発見した場合は、SIT-CSIRTまでご報告いただけます様お願いいたします。
SIT-CSIRT
csirt@shibaura-it.ac.jp
We have confirmed that a fake website impersonating our university appears in the search results when you search for keywords related to our university through search engines.
Not only in this case, but also in other recent cases, fake sites have been appearing in search results.
Some of the fake sites may infect web browsers or download malware when accessed, so please be sure to always check your search results for suspicious items.
If you find a fake site, please report it to SIT-CSIRT.
SIT-CSIRT
csirt@shibaura-it.ac.jp
Example of search results
 |
Examples of Fake Sites
 |
Dear students, faculty and staff
This is a notice from the Information Systems Division.
There has been an increase in the number of phishing e-mails sent to you by people trying to defraud you of your account information for commercial Internet services or for the University.
Some of these emails may slip through our email security system and be delivered to you.
Users have reported receiving suspicious e-mails.
If you receive a suspicious e-mail, be careful not to access the URL in the body of the message.
Do not open any attached files.
The sender (From:) is often spoofed and may be the sender's own email address or the administrator's email address (e.g., admin@~).
An example of a subject line: sic.shibaura-it
sic.shibaura-it.ac.jp New Webmail service is now available
mail delivery failure: storage is almost full
ow.shibaura-it.ac.jp mail service update Case ID: ?????
You have [13] pending incoming emails
SYSTEM NOTIFICATION ~ Your 8 unreceived emails are stuck on the sic.shibaura-it.ac.jp Server.
Your ow.shibaura-it.ac.jp Account will be disabled soonest.
Your Outlook storage is full
Verify User
Mail Notice: De-activation
Account Termination
Email Termintaion Request
Undeliverable: Incoming messages failure
Check Password
Email Verification ~ VERIFY YOUR EMAIL ACCOUNT TODAY
~Unknown Login Notification
Password Expiration Notice!
~ Email Notification
Required Action: Email Deactivation Notification for
Required Action: Important Notification for Tuesday, June 27, 2023
Required Action: Important Notification for Monday, June 26, 2023
Required Action: Important Notification for Sunday, June 25, 2023
You have received a new voicemail memo.
Error receiving mail
Notification: Mailbox size has reached quota limit
Sic mailbox size has reached quota limit
Mailbox storage space is low
~ Received Mail Error
Mailbox storage is full, account is suspended
If you receive a suspicious email, please contact SIT-CSIRT.
SIT-CSIRT (Shibaura Institute of Technology Computer Security Incident Response Team)
Email: csirt@shibaura-it.ac.jp
Translated with www.DeepL.com/Translator (free version)
Emotet is malware that is often infected by opening Word files attached to emails.
It was seized and stopped by EUROPOL (European Organization of the Criminal Police) on 1/27/2021, but there are signs of resumption of activity since around 11/14/2021.
The attached files are not only Word and Excel files, but also zip files with passwords.
Emotet malware, which was popular in Japan from the end of August 2019 to January 2020, seems to have temporarily resumed its activities in Japan since July 2020. Please be aware that activities may become more active in the future.
When infected with Emotet, not only is the e-mail information of Outlook (authentication information to the e-mail server, e-mail address of the inbox, subject etc.) stolen, but also other malware (Qbot, TrickBot, Ryuk ransomware, Ursnif banking malware etc.) ) May cause additional infections.
The stolen email information may be used to scatter emails to spread infection.
Please note that there are various subject lines for emails, and some may take the form of replies to stolen emails.
If you receive such an email, please do not open it and contact the Center for Science Information.
If you open it and activate the content, immediately disconnect from the network.
Please check if the antivirus software on your device is working properly.
【Attention】
For the emails scattered,there are those that take the form of replying by quoting stolen mail in the body (reply type), and those that embed the stolen name/email address etc. in the subject and signature of the body.
Please be careful.
It has been confirmed that there is no attached file and a link is written in the email body.
Please be careful not to access the link destination as the Word file etc. of the Emotet downloader will be downloaded when you click the link.
!!!Do not run macros in Word files with macros (do not press enable content)!!!
【Information about Emotet】
Sender
(People who have exchanged in the past)
Example of subject
Request to send invoice (number etc.)
This is the invoice. (Numbers, etc.)
Re: (Subject of previously received email)
Example of attachment file name
(Alphabet and numbers) Please send invoice. doc
(Alphabet or number) This is the invoice. .doc
(Alphabets and numbers) Notification of payment amount and issuance of invoice.doc
Dear Faculty and Staff
This is a notice from the Information Network Service Section.
During the year-end and New Year holidays, security incidents are more likely to occur due to the lack of system management.
As the volume of e-mails checked will increase, please be especially careful of suspicious e-mails after the holidays,
In recent years, A number of cyber-attacks confirmed by fake e-mails sent to Japanese academics, think tank researchers, and the press, pretending to be requests for lectures or interviews, etc., and leading to be compromised by executing malware, then attempt to steal the contents of emails and computer files exchanged by these individuals.
For details, please refer to the information provided by the National Police Agency's Cybercrime Countermeasures Project.
( https://www.npa.go.jp/cyber/ )
Our university introduced an e-mail targeted attack countermeasure system for full-time faculty and administrative staff.
Suspicious e-mails are automatically quarantined and a notification e-mail is sent at 15:00 daily,
so please make sure to check the contents.
https://web.sic.shibaura-it.a
If you receive a suspicious email, please contact SIT-CSIRT.
SIT-CSIRT (Shibaura Institute of Technology Computer Security Incident Response Team)
Email: csirt@shibaura-it.ac.jp