2025/06/20 [重要] フィッシングメールに注意
本日下記のようなフィッシングメールが本学あてに送信されて来ています。
件名:
ドキュメント「支払確認領収書.pdf」がOneDrive経由で共有されました
メール本文のリンクはクリックしないようにしてください。
うっかりフィッシングサイトにパスワードを入力してしまった場合は、すぐにパスワードを変更し、最寄りの情報イノベーション課までご連絡ください。

本日下記のようなフィッシングメールが本学あてに送信されて来ています。
件名:
ドキュメント「支払確認領収書.pdf」がOneDrive経由で共有されました
メール本文のリンクはクリックしないようにしてください。
うっかりフィッシングサイトにパスワードを入力してしまった場合は、すぐにパスワードを変更し、最寄りの情報イノベーション課までご連絡ください。
検索サイトから本学に関連するキーワードを検索すると、本学を騙る偽サイトが検索結果に表示されることを確認いたしました。
本件に限らず、最近検索結果に偽サイトが表示されることが散見されます。
偽サイトの中にはアクセスをするとWebブラウザに感染するものや、マルウエアがダウンロードされるものも存在しますので、常に検索結果に不審なものが含まれていないか確認することを心掛けてください。
また、偽サイトを発見した場合は、SIT-CSIRTまでご報告いただけます様お願いいたします。
SIT-CSIRT
csirt@shibaura-it.ac.jp
We have confirmed that a fake website impersonating our university appears in the search results when you search for keywords related to our university through search engines.
Not only in this case, but also in other recent cases, fake sites have been appearing in search results.
Some of the fake sites may infect web browsers or download malware when accessed, so please be sure to always check your search results for suspicious items.
If you find a fake site, please report it to SIT-CSIRT.
SIT-CSIRT
csirt@shibaura-it.ac.jp
Example of search results
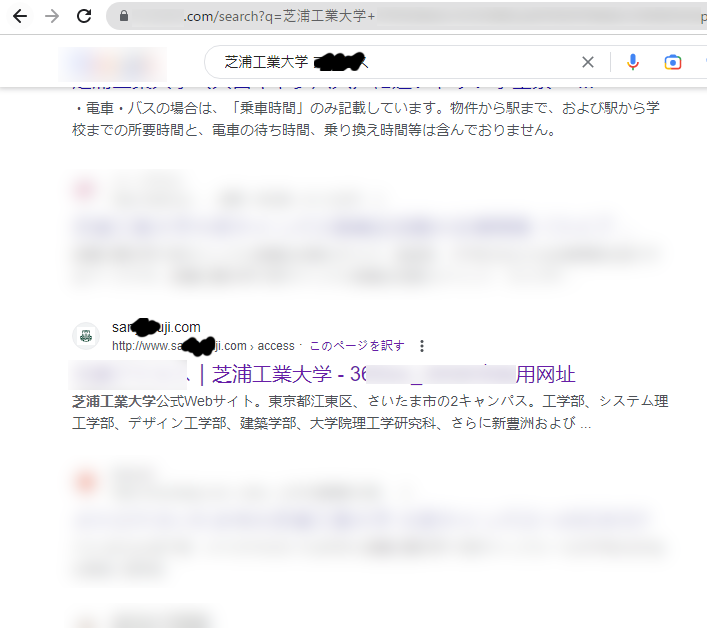 |
Examples of Fake Sites
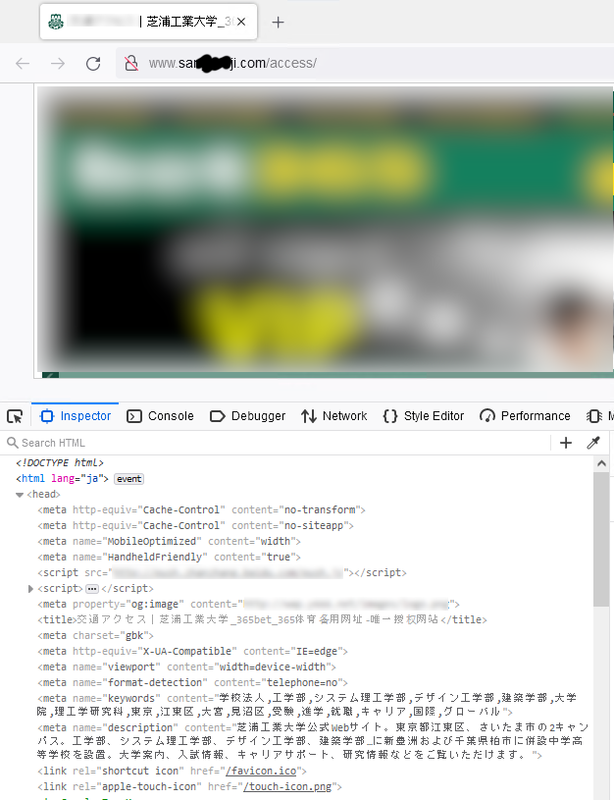 |
Dear students, faculty and staff
This is a notice from the Information Systems Division.
There has been an increase in the number of phishing e-mails sent to you by people trying to defraud you of your account information for commercial Internet services or for the University.
Some of these emails may slip through our email security system and be delivered to you.
Users have reported receiving suspicious e-mails.
If you receive a suspicious e-mail, be careful not to access the URL in the body of the message.
Do not open any attached files.
The sender (From:) is often spoofed and may be the sender's own email address or the administrator's email address (e.g., admin@~).
An example of a subject line: sic.shibaura-it
sic.shibaura-it.ac.jp New Webmail service is now available
mail delivery failure: storage is almost full
ow.shibaura-it.ac.jp mail service update Case ID: ?????
You have [13] pending incoming emails
SYSTEM NOTIFICATION ~ Your 8 unreceived emails are stuck on the sic.shibaura-it.ac.jp Server.
Your ow.shibaura-it.ac.jp Account will be disabled soonest.
Your Outlook storage is full
Verify User
Mail Notice: De-activation
Account Termination
Email Termintaion Request
Undeliverable: Incoming messages failure
Check Password
Email Verification ~ VERIFY YOUR EMAIL ACCOUNT TODAY
~Unknown Login Notification
Password Expiration Notice!
~ Email Notification
Required Action: Email Deactivation Notification for
Required Action: Important Notification for Tuesday, June 27, 2023
Required Action: Important Notification for Monday, June 26, 2023
Required Action: Important Notification for Sunday, June 25, 2023
You have received a new voicemail memo.
Error receiving mail
Notification: Mailbox size has reached quota limit
Sic mailbox size has reached quota limit
Mailbox storage space is low
~ Received Mail Error
Mailbox storage is full, account is suspended
If you receive a suspicious email, please contact SIT-CSIRT.
SIT-CSIRT (Shibaura Institute of Technology Computer Security Incident Response Team)
Email: csirt@shibaura-it.ac.jp
Translated with www.DeepL.com/Translator (free version)
Emotet is malware that is often infected by opening Word files attached to emails.
It was seized and stopped by EUROPOL (European Organization of the Criminal Police) on 1/27/2021, but there are signs of resumption of activity since around 11/14/2021.
The attached files are not only Word and Excel files, but also zip files with passwords.
Emotet malware, which was popular in Japan from the end of August 2019 to January 2020, seems to have temporarily resumed its activities in Japan since July 2020. Please be aware that activities may become more active in the future.
When infected with Emotet, not only is the e-mail information of Outlook (authentication information to the e-mail server, e-mail address of the inbox, subject etc.) stolen, but also other malware (Qbot, TrickBot, Ryuk ransomware, Ursnif banking malware etc.) ) May cause additional infections.
The stolen email information may be used to scatter emails to spread infection.
Please note that there are various subject lines for emails, and some may take the form of replies to stolen emails.
If you receive such an email, please do not open it and contact the Center for Science Information.
If you open it and activate the content, immediately disconnect from the network.
Please check if the antivirus software on your device is working properly.
【Attention】
For the emails scattered,there are those that take the form of replying by quoting stolen mail in the body (reply type), and those that embed the stolen name/email address etc. in the subject and signature of the body.
Please be careful.
It has been confirmed that there is no attached file and a link is written in the email body.
Please be careful not to access the link destination as the Word file etc. of the Emotet downloader will be downloaded when you click the link.
!!!Do not run macros in Word files with macros (do not press enable content)!!!
【Information about Emotet】
Sender
(People who have exchanged in the past)
Example of subject
Request to send invoice (number etc.)
This is the invoice. (Numbers, etc.)
Re: (Subject of previously received email)
Example of attachment file name
(Alphabet and numbers) Please send invoice. doc
(Alphabet or number) This is the invoice. .doc
(Alphabets and numbers) Notification of payment amount and issuance of invoice.doc
Dear Faculty and Staff
This is a notice from the Information Network Service Section.
During the year-end and New Year holidays, security incidents are more likely to occur due to the lack of system management.
As the volume of e-mails checked will increase, please be especially careful of suspicious e-mails after the holidays,
In recent years, A number of cyber-attacks confirmed by fake e-mails sent to Japanese academics, think tank researchers, and the press, pretending to be requests for lectures or interviews, etc., and leading to be compromised by executing malware, then attempt to steal the contents of emails and computer files exchanged by these individuals.
For details, please refer to the information provided by the National Police Agency's Cybercrime Countermeasures Project.
( https://www.npa.go.jp/cyber/ )
Our university introduced an e-mail targeted attack countermeasure system for full-time faculty and administrative staff.
Suspicious e-mails are automatically quarantined and a notification e-mail is sent at 15:00 daily,
so please make sure to check the contents.
https://web.sic.shibaura-it.a
If you receive a suspicious email, please contact SIT-CSIRT.
SIT-CSIRT (Shibaura Institute of Technology Computer Security Incident Response Team)
Email: csirt@shibaura-it.ac.jp
Dear Students, Faculty and Staff
Warning from the Information Network Service Division
We have received many reports of suspicious Emotet malware email from several people today.
We announced this on November 25 last year, but we would like to ask you to check again.
Please also check the security information on the Center for Science Information website.
1. Warning against phishing e-mails
Recently, there have been many cases of phishing e-mails aimed at fraudulently obtaining account information for webmail services.
We have also received reports of suspicious emails from users of our university.
If you receive a suspicious email, please be careful not to access the URL in the text.
If you receive a suspicious e-mail, please do not access the URL in the text, and do not open any attachments.
Please check the security information on the Center For Science Information website.
Example of subject line:
メールプラン、セキュリティ強化第2弾リリースのお知らせ
【重要】2021年XX月XX日(X)のサービス復旧のお知らせ。
【重要】使用制限によるサービス停止のお知らせ- {メールアドレス}
【重要】サービス停止のお知らせ - {メールアドレス}
【お知らせ】メール配信通知 - {メールアドレス}
[メール接続サービスの終了について_shibaura-it.ac.jp] - {メールアドレス}
[からの通知_Shibaura-it]_{メールアドレス}
【バージョンアップ】メンテナンス作業のお知らせ
【重要】sic.shibaura-it.ac.jp メール送信機能停止のお知らせ
If you receive a suspicious email, please contact SIT-CSIRT.
SIT-CSIRT (Shibaura Institute of Technology Computer Security Incident Response Team)
Email: csirt@shibaura-it.ac.jp
2. Warning about Emotet malware email
The Emotet malware was seized and stopped by EUROPOL (European Criminal Police Organization) on January 27, 2021.
However, it has tended to resume its activities since around November 14, 2021.
It seems that emails targeting Japan are also being sent.
For more information about the Emotet malware, please check the security information on the Center For Science Information website.
If you receive a suspicious email, please contact SIT-CSIRT.
SIT-CSIRT (Shibaura Institute of Technology Computer Security Incident Response Team)
Email: csirt@shibaura-it.ac.jp 3.
3. Warning about attacks on the CMS of web servers
If you are running a web server in your laboratory and using CMS (WordPress, Movable Type, etc.)
Please check for suspicious access.
In Japan, there have been cases of illegal content being embedded, phishing e-mails being sent out in large numbers, and unauthorized server intrusions.
Please take measures such as managing passwords for the web servers you use, updating vulnerable software, and stopping unnecessary services.
If you find any suspicious access, please contact SIT-CSIRT.
SIT-CSIRT (Shibaura Institute of Technology Computer Security Incident Response Team)
Email: csirt@shibaura-it.ac.jp
There have been reports of suspicious e-mails being sent from your own e-mail address.
The sender's email address may have been spoofed to match that of the recipient.
Reference Information(Japanese):
There are many different subject lines, as shown below. (Japanese)
These are threatening or fraudulent emails. If you receive such an email, please discard it.
Example 1(Japanese):
それが起こったのです。ゼロクリックの脆弱性と特別なコードを使用して、Webサイトを介してあなたのデバイスをハッキングしました。私の正確なスキルを必要とする複雑なソフトウェア。このエクスプロイトは、特別に作成された一意のコードを使用してチェーンで機能し、このようなタイプの攻撃は検出されません。Webサイトにアクセスしただけで感染してしまいましたが、残念なことに、私にとっては非常に容易いことです。あなたは標的にされたのではなく、そのWebページを介してハッキングされた多くの不運な人々の一人になったのです。これはすべて8月に起こりました。そのため、情報収集には十分な時間がありました。次に何が起こるかはもうご存知だと思います。数ヶ月間、私のソフトウェアは、あなたの習慣、あなたが訪問するウェブサイト、ウェブ検索、あなたが送るテキストなどの情報を静かに収集していました。他にもまだまだありますが、これがどれほど深刻であるかを理解していただくために、いくつかの理由を挙げました。
(以下省略)
That's what happened. Using a zero-click vulnerability and special code, I hacked your device through a website. Complex software that requires my exact skills. This exploit works in a chain using a specially created unique code and this type of attack is undetectable. just visiting the website infected me, unfortunately it is very easy for me. You were not targeted, but became one of the many unlucky people who were hacked through that web page. This all happened in August. Therefore, there was plenty of time to gather information. I think you already know what will happen next. For months, my software has been quietly collecting information about your habits, websites you visit, web searches, texts you send, and so on. There are many more, but I have listed a few reasons to help you understand just how serious this is.
(Omitted below)
Example 2(Japanese):
それが起こったのです。ゼロクリックの脆弱性と特別なコードを使用して、Webサイトを介してあなたのデバイスをハッキングしました。 私の正確なスキルを必要とする複雑なソフトウェア。 このエクスプロイトは、特別に作成された一意のコードを使用してチェーンで機能し、このようなタイプの攻撃は検出されません。 Webサイトにアクセスしただけで感染してしまいましたが、残念なことに、私にとっては非常に容易いことです。 あなたは標的にされたのではなく、そのWebページを介してハッキングされた多くの不運な人々の一人になったのです。 これはすべて8月に起こりました。そのため、情報収集には十分な時間がありました。 次に何が起こるかはもうご存知だと思います。 数ヶ月間、私のソフトウェアは、あなたの習慣、あなたが訪問するウェブサイト、ウェブ検索、あなたが送るテキストなどの情報を静かに収集していました。 他にもまだまだありますが、これがどれほど深刻であるかを理解していただくために、いくつかの理由を挙げました。 明確に言うと、私のソフトウェアはあなたのカメラとマイクも制御しました。
(以下省略)
That's what happened. Using a zero-click vulnerability and special code, I hacked your device through a website. Complex software that requires my exact skills. This exploit works in a chain using a specially created unique code and this type of attack is undetectable. I got infected just by visiting a web site, unfortunately, it is very easy for me. You were not targeted, but became one of the many unlucky people who were hacked through that web page. This all happened in August. Therefore, there was plenty of time to gather information. I think you already know what will happen next. For months, my software has been quietly collecting information about your habits, websites you visit, web searches, texts you send, and so on. There are many more, but I have listed a few reasons to help you understand how serious this is. To be clear, my software also took control of your camera and microphone.
(Omitted below)
例3:
"Let's resolve it like this: All you need is $1750 USD transfer to my account (bitcoin equivalent based on exchange rate during your transfer), and after the transaction is successful, I will proceed to delete all that kinky stuff without delay. Afterwards, we can pretend that we have never met before. In addition, I assure you that all the harmful software will be deleted from all your devices. Be sure, I keep my promises." I think that about sums it up.
Dear Students, Faculty and Staff
Warning from the Information Network Service Division
We would like to inform you that we have received three reminders from the Cyber Security Division of the Ministry of Education, Culture, Sports, Science and Technology.
1. Warning against phishing e-mails
Recently, there have been many cases of phishing e-mails aimed at fraudulently obtaining account information for webmail services.
We have also received reports of suspicious emails from users of our university.
If you receive a suspicious email, please be careful not to access the URL in the text.
If you receive a suspicious e-mail, please do not access the URL in the text, and do not open any attachments.
Please check the security information on the Center For Science Information website.
Example of subject line:
メールプラン、セキュリティ強化第2弾リリースのお知らせ
【重要】2021年XX月XX日(X)のサービス復旧のお知らせ。
【重要】使用制限によるサービス停止のお知らせ- {メールアドレス}
【重要】サービス停止のお知らせ - {メールアドレス}
【お知らせ】メール配信通知 - {メールアドレス}
[メール接続サービスの終了について_shibaura-it.ac.jp] - {メールアドレス}
[からの通知_Shibaura-it]_{メールアドレス}
【バージョンアップ】メンテナンス作業のお知らせ
【重要】sic.shibaura-it.ac.jp メール送信機能停止のお知らせ
If you receive a suspicious email, please contact SIT-CSIRT.
SIT-CSIRT (Shibaura Institute of Technology Computer Security Incident Response Team)
Email: csirt@shibaura-it.ac.jp
2. Warning about Emotet malware email
The Emotet malware was seized and stopped by EUROPOL (European Criminal Police Organization) on January 27, 2021.
However, it has tended to resume its activities since around November 16, 2021.
It seems that emails targeting Japan are also being sent.
For more information about the Emotet malware, please check the security information on the Center For Science Information website.
If you receive a suspicious email, please contact SIT-CSIRT.
SIT-CSIRT (Shibaura Institute of Technology Computer Security Incident Response Team)
Email: csirt@shibaura-it.ac.jp 3.
3. Warning about attacks on the CMS of web servers
If you are running a web server in your laboratory and using CMS (WordPress, Movable Type, etc.)
Please check for suspicious access.
At other universities, there have been cases of illegal content being embedded, phishing e-mails being sent out in large numbers, and unauthorized server intrusions.
Please take measures such as managing passwords for the web servers you use, updating vulnerable software, and stopping unnecessary services.
If you find any suspicious access, please contact SIT-CSIRT.
SIT-CSIRT (Shibaura Institute of Technology Computer Security Incident Response Team)
Email: csirt@shibaura-it.ac.jp
If your laboratory operates a web server and uses a CMS (WordPress, Movable Type, etc.), please check for suspicious access.
In Japan, incidents such as the embedding of malicious content, mass transmission of phishing e-mails, and unauthorized intrusion into servers have occurred.
Please take measures such as managing passwords for the web server you are using, updating vulnerable software, and stopping unnecessary services.
WordPress Vulnerability Information
Movable Type Vulnerability Information
不審なアクセスを発見した場合は、SIT-CSIRTに連絡してください。
SIT-CSIRT (Shibaura Institute of Technology Computer Security Incident Response Team)
Email: csirt@shibaura-it.ac.jp
Recently, phishing e-mails posing as e-mail systems have been sent to many organizations.
Subject Example:
The following screen is not the login screen for the system used by the university.
Never enter your email address or password.
Please contact the Information System Division if you have inadvertently typed something.
We have received a report that phishing e-mails are being sent to several e-mail addresses of the University of Tokyo at around 8:33 a.m. on September 29, 2021, falsely claiming to be notices of maintenance work on the Webmail system.
If you enter your user name and password into this site, your credentials may be exploited and unauthorized access may be gained.
If you have inadvertently entered your username and password, please change your password and contact the Information System Division.
If you have inadvertently entered your username and password, please change your password and contact the Information System Division.
・Example subject line(Japanese)
|
【アップグレード】メンテナンス工事のお知らせ(2021年9月29日(水)) 【重要】2021年9月29日水曜日のサービス復旧の通知。 |
・Example of main text(Japanese)
|
お客様各位 平素は弊社shibaura-it.ac.jpインターネットサービスをご利用いただきまして誠にありがとうございます。 2021年9月29日 **:**-**:**~ 以下の対象サーバーを使用しているお客様で障害が発生しました。 現在は復旧しております。 ■対象サーバー ■時間 ■内容 ■原因 メールサーバーを認証するには、以下のリンクをクリックしてください https://~~~.xyz/1Lulu/access/online/user?uid=~~~@shibaura-it.ac.jp 認証されていない場合、[[-Domain-]]インターネットルーティングのすべてのサービスが中断されます。 |
|
発生しておりましたが、修復作業は、2021年9月29日水曜日の午前8時頃に始まりました。 ウェブメールサービスを復元するには、次のURLを参照してください。 https://~~~~~~~~.com/Hos/Hos2?uid=~~~~@shibaura-it.ac.jp
今後もお客さまの期待と信頼にお応えするため、運営ならびにサービスの充実に |
・Example of a phishing site screen
We have received several inquiries like this.
"When browsing internet sites, screens such as "Access to this PC is blocked for security reasons" or "Windows was blocked due to suspicious activity" are displayed with alarm sounds."
Both will prompt you to call a phone number starting with 050, and when you call, you will be instructed to install remote control software or go to a convenience store to buy a prepaid card.
This is a support scam.
Virus infection warning and support phone number displayed
https://www.keishicho.metro.tokyo.jp/sodan/nettrouble/jirei/warning_screen.html
Click here for how to close the fake warning screen.
Microsoft :
https://news.microsoft.com/ja-jp/2021/01/29/210129-information/
If the display does not stop even after closing the browser, please contact SIT Center for Science Information.
How to contact us :
https://web.sic.shibaura-it.ac.jp/otoiawase?lang=en
We've received calls that suspicious emails with attachments were sent to SIT email addresses from 2020/07/08 1:55.
This attached file make your computer infected to ransomwarewhen you open the file.
When you receive this email, please delete the email WITHOUT open/download attached file.
When you inadvertently open the attached file, please call Center for Science Information!
Examples of Subject
Examples of attatched file name
IMG[Numbers].jpg.js.zip
2020/04/21 From around 11:47, there were reports that the phishing emails of the Webmail-like system were distributed to multiple email addresses of our university.
If you enter your user name and password on this site, your authentication information may be exploited, which may lead to unauthorized access.
If you receive this email, please delete it without accessing the link.
If you accidentally enter your user name and password, please change your password and contact the Information Systems Division.
| [Version up] Notification of maintenance work [April 21, 2020] |
|
Dear customer Thank you for using [Sic] Internet service. We are carrying out server maintenance. Follow the link below to upgrade your service https: //~~~ems.ru/jp/webmail-op.jp? uid = ~~~ Copyright (C) Sic Co., Ltd. All Rights Reserved. |
2020/04/19 From around 02:26 to around 02:30, and from around 04:04 to around 04:09, phishing e-mails disguised as the University's WebActive! Mail were scattered to multiple e-mail addresses. Was reported.
When you access the link in the body of the email, you will see a website that looks just like the University's Webmail system.
If you enter your user name and password on this site, your authentication information may be exploited, which may lead to unauthorized access.
If you receive this email, please delete it without accessing the link.
If you accidentally enter your user name and password, please change your password and contact the Information Systems Division.
| Re: Active! Email update! |
| Re: Confirmation Mail |
|
Dear users, Your active! Email. Mailboxes have exceeded the storage limits set by the administrator and new mail cannot be sent or received until the mailbox is revalidated. And it costs you nothing. To revalidate-click here
|
|
Dear User, Your Active!mail. mailbox has exceeded it's storage limit as set by your administrator and you will not be able to send and receive new mails until you re-validate it. And it will not cost you anything. To re-validate - click here Thank you. |
2020/04/15 From around 12:06, there were reports that phishing e-mails, which seem to be web mails, were distributed to multiple e-mail addresses of our university.
If you enter your user name and password on this site, your authentication information may be exploited, which may lead to unauthorized access.
If you receive this email, please delete it without accessing the link.
If you accidentally enter your user name and password, please change your password and contact the Information Systems Division.
| [Upgrade] Notification of maintenance work [April 14, 2020] |
|
Dear customer Thank you for using [Sic] Internet service. We are carrying out server maintenance. Follow the link below to upgrade your service https://~~~.com/jp/webmail-op.jp?uid=~~~ Copyright (C) Sic Co.,Ltd. All Rights Reserved. |
From around 2020/02/11 12:08, there were reports that phishing emails spoofing the University's WebActive! Mail were being scattered to multiple university email addresses.
When you access the link in the body of the e-mail, a site similar to the university's Web mail system will be displayed.
If you enter your username and password on this site, your credentials will be exploited and unauthorized access may be possible.
If you receive this email, please delete it without accessing the link.
If you accidentally enter your user name and password, change the password and contact the Information System Section.
| RE: Please confirm your account |
|
Your mailbox is almost full. 9407MB 3GB Click https://mailactive.legalsaudi~(省略)~ to verify your account. |
Around 8:30 2020/02/08 and around 12:31 2020/02/11 there have been reports that suspicious e-mails with emoticons in the subject and body have been scattered to multiple e-mail addresses of the University. did.
When the attached file is opened, it is infected with ransomware (NEMTY), the data is encrypted and a ransom is required.
If you receive this email, please delete the attachment without opening it.
If you accidentally get infected and your data is encrypted, please contact the Information Systems Section.
Report that phishing e-mails spoofing the University's WebActive! Mail are distributed to multiple e-mail addresses of the University around 2020/01/30 23:47 and 01/31 01: 20-02: 28 had.
When you access the link in the body of the e-mail, a site similar to the university's Web mail system will be displayed.
If you enter your username and password on this site, your credentials will be exploited and unauthorized access may be possible.
If you receive this email, please delete it without accessing the link.
If you accidentally enter your user name and password, change the password and contact the Information System Section.
| Upgrade an active email account |
|
Your MALLB0X is out of date https: //activemail.amsteel-finance.~~~ Thank you, active! Webmail team |
Since the end of August 2019, Emotet Malware has been in fashion in Japan. Emotet is malware that is often infected by opening Word files attached to e-mails.
If you get infected with Emotet, you will not only steal Outlook email information (email server authentication information, inbox email address, subject, etc.) but also to other malware (TrickBot, Ryuk ransomware, Ursnif banking malware, etc.) Additional infection may occur.
The stolen email information may be used to disseminate emails for spreading infection.
Please note that the subject line of emails varies and some of them take the form of replies to stolen emails.
If you receive such an email, please do not open it and contact the Information Systems Division.
If you open it and activate the content, disconnect from the network immediately.
Please make sure that the anti-virus software on your device is operating correctly.
件名の例
| Cambiar los terminos de pago de sus servicios de Ma Jose Cambion de su tarifa de Ma Jose Su tarifa para confirmacion de Ma Jose Agreement Application pack ~ (date and name) Comments Comments for Compliance report Compliance report-(date and name) Confirmation-(date and name) Customer Feedback Information-(date and name) Customer Feedback Information for (Name) Customer Statement Documents Enquiry (date and name) Inquiry for Facturacion Naturgy Feedback Information Files (date and name) FW: Scan from a Huawei MFP Fwd: RE: Re: Shipment Document General Inquiry for (Name) Hello INFO (PRODUCTION)-(Name) INVOICE JLL2019-0095 Invoice n (date) La documentation d'avril d ’(date) List List-(Name) Mail from (date and name) Notice Notice for Notre reponse-(date) Notre reponse d ’(date) RE: ***** SPAM *****-Thanks For Your Effort So !! RE: *** SPAM *** Thanks For Your Effort So !! Re: Darlehen! Re: Hello RE: SOA-Long Overdue Invoices Renewals-(Name) Report (date) Request for quotation RFQ for (Name) RV: ***** SPAM *****-Thanks For Your Effort So !! Scan Data-(Date and name) Scan Data for (Name) Service (date) Signed Agreement (date) Statement-(name) Statement (date) (name) URGENT MESSAGE URGENT MESSAGE (date) comment Comment (Name) data Data (Name) document Document (date and name) message Message (date or name) Repeat message Repeat message (name) reminder List (Name) Remarks Remarks (date and name) help Help (date and name) information Information (date and name) New version New version (date and name) Last option Last option (date or name) Current version Current version (date and name) |